DORA-TLPT (Threat-Led Penetration Testing) requirements are live in January 2025! Most TLPT assessments are likely to be adaptations of TIBER-EU and/or UK-CBEST frameworks, which are complex, long-term red team engagements involving multiple formal parties with separation of duties and structured outputs.
VECTR™ is widely known as a great platform for documenting and benchmarking Purple Teams / Threat Simulations, but it also has Red Team utility that can apply directly to TLPT engagements.
The first part of a TLPT engagement is the Threat Intel report. VECTR™ does not produce a full intel report but using the heatmap may help you show the output of your Intel phase and how it connects to the Red Team phase. This MITRE ATT&CK map in VECTR™ shows the known techniques used by APT28, Scattered Spider, Akira, Black Basta and BlackCat. This could be any groups described by MITRE or that you input into your VECTR™ system.

Example expanded heatmap showing threat groups to be modeled resulting form the Intel phase
This can then be translated into a Red Team campaign plan in VECTR™. Note that the heatmap above and the TTPs in the example are from my demo so not a 1-1 match. VECTR™ allows us to break our intel heatmap into several different Red Team “campaigns” if we choose, which is helpful in separating External from Internal and other scenarios.
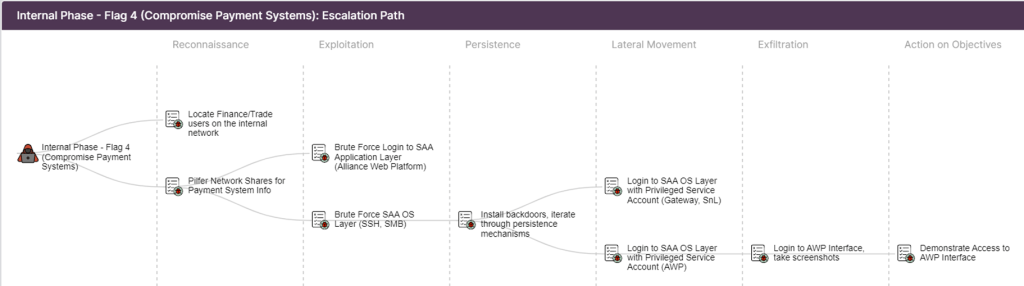
Example Red Team plan in VECTR™ focused on SWIFT payment systems
An important aspect of TLPT testing is the separation of access and role-based knowledge of the test, especially because the Blue Team cannot have knowledge of the test while it’s ongoing. We can configure Groups, Users, Access Policies and even SSO.
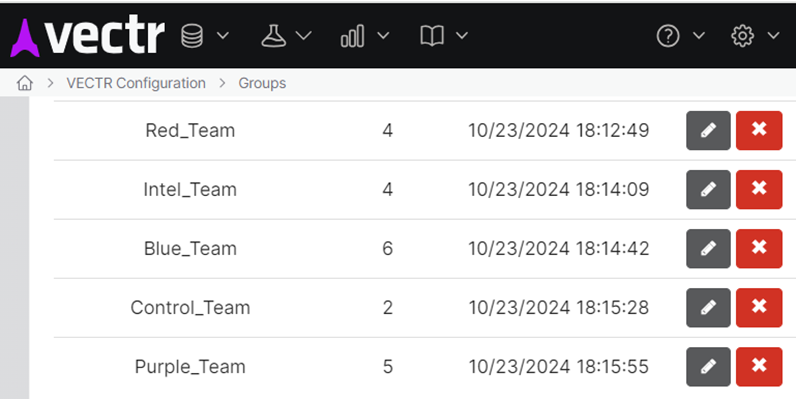
We can create groups in a TLPT starting with Intel, Blue, Control, Red and Purple and restrict access to test plans and results based on those.
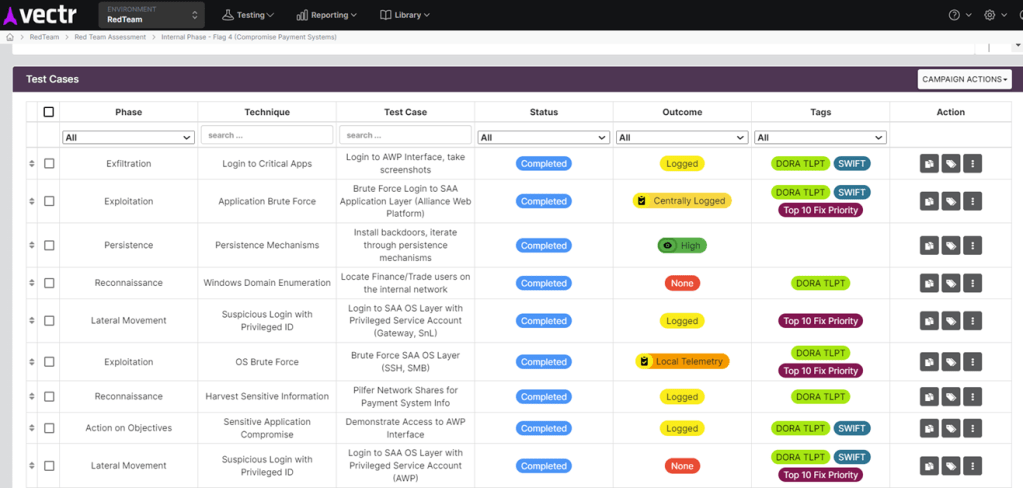
VECTR™ lets the Red Team document their TTPs in a structured way. While not required as part of DORA-TLPT, this can allow more detailed post mortem review with the Blue Team, or this can be done collaboratively in a Purple Team phase. We have time stamps, exact Operator syntax, detailed outcome notes and “Tags” to inform further reporting and remediation plans.

VECTR excels at reporting and shows us the results of every documented Red Team operation / step. Note that the use of VECTR™ Tags here lets us do further sorting, for example to view only the test cases having to do with TLPT + SWIFT, or any other combinations relevant to the organization. It also allows a TLPT test plan to remain among other Red or Purple teams work that VECTR™ users may perform. In this sense, VECTR™ is far more useful than just for DORA-TLPT but also serves as a “security test case repository” for the organization, throughout the year.
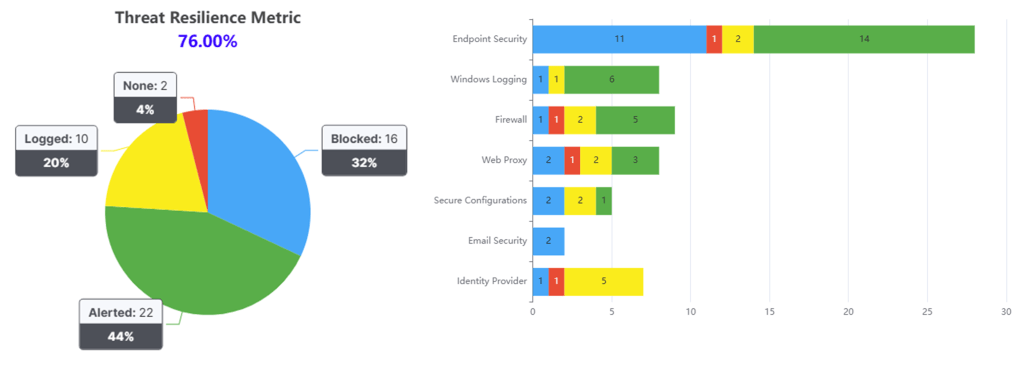
VECTR™ has other reporting views such as the Threat Resilience Metric showing the overall success of the Blue Team vs. the TLPT, and security tool efficacy (made general in this example) where Blue = Blocked, Green = Alerted, Yellow = Logged but not Alerted and Red = Full Gap.
VECTR™ is not a silver bullet to meet all your DORA-TLPT reporting needs, but it is a very useful reporting aide. If you have more ideas for how it can further align to TLPT needs, don’t hesitate to reach out.
All VECTR™ Enterprise clients can use VECTR™ for DORA-TLPT. If you are a consultancy or being charged fees by a consultancy, please refer to the EULA for guidance on use of VECTR™ Community and reach out to the VECTR™ team for a quote. VECTR™ Community edition remains free for educational, internal use and training purposes.






