
Benchmarking Detection,
Automating Resilience, and
Optimizing Security Spend.
Security Risk Advisors’ SCALR™ XDR is both a platform and a 24×7 monitoring service. SCALR™ XDR uses a security data lake architecture to minimize SIEM costs, maximizing your ability to store security events, and accelerate search and hunting capabilities. The SCALR™ XDR service is enhanced by SCALR™ AI and our distinctive Purple Teams & Threat Resilience Benchmarks.

Security Risk Advisors (SRA) has partnered with the International Rescue Committee (IRC), the global non-profit organization that helps people affected by humanitarian crises. The IRC helps people affected by humanitarian crises to survive, recover and rebuild their lives in over 40 countries.
SRA is providing the SCALR™ XDR CyberSOC service at no cost to the IRC in support of their important global efforts.
Cloud SIEM is expensive!
The shift to cloud-based SIEMs has resulted in consumption-based pricing. The more you use, the more you pay.
SCALR™ XDR’s optimized data pipeline combined with an integrated data lake can dramatically reduce your overall spend.
Purple Team testing enables continuous improvement to your security detection and response capabilities with metrics that prove it.
SCALR™ XDR can extend your long-term data retention by as much as 4x the industry average.
SCALR™ XDR can reduce technology spend by 75% on average over other cloud or on-premise SIEM.
Discover the Total Economic Impact™ of SCALR XDR
A commissioned study conducted by Forrester Consulting on behalf of Security Risk Advisors revealed how SCALR XDR benefited a composite organization representative of interviewed customers.
Learn how SCALR clients have overcome compounding cloud technology costs while protecting their organizations from cyberattacks.

264%
return on investment
$2,900,000
avoided cost of legacy solution
$2,000,000
in avoided costs of internal staff
$1,600,000
reduced risk of security incidents
* For the purposes of this study, Forrester aggregated the interviewees’ experiences and combined the results into a single composite organization with 10,000 employees, revenue of $2 billion per year, and daily security information and event management (SIEM) ingestion of 800 GB.
Operated and managed 24x7x365
Monitoring & Response by SRA’s skilled team of analysts. We deliver a threat-driven program that proactively identifies needs and works with your team to implement new detections.
SIEM
A turnkey serverless cloud environment with pre-configured and continually-expanding detections.
Data Lake
A modern, scalable and cost-effective data lake model for your security data.
SOAR
Security automation as a first-class feature of your detection and response process.
SCALR AI
Whether you have Security Copilot or not, as an SRA SCALR XDR client you still get SCALR AI
Purple Teams
Collaborative, open-book testing of your defensive controls.
Tier 0 Support with SCALR AI

The CISO’s teams are expected to meaningfully adopt AI and the CISO must be able to describe gains, benefits, and costs with their C-suite peers.
SCALR AI is a multi-agentic workflow engine for large, complex task execution in your SRA-powered SCALR XDR Security Operations Center.
Your people will automate and execute previously time-consuming and error-prone tasks in security operations, vulnerability management, devops, threat hunting, content development and more.
Don’t buy AI and get trapped in yet another startup vendor box – your team needs to learn to build AI with a flexible, private tenant cloud native platform. Leverage the cost-effective Azure AI Foundry and connect to other cloud services and partners.
CISOs can show tangible AI gains when sitting among their peer executives.
Use Cases
- Log Health Monitor & Alert: Identify, report and help fix log source anomalies that may indicate downed sources
- Incident Enrichment: Automatically add internal and external context to alerts to enhance MTTA and MTTR
- Daily SOC Summary and Analysis: Receive daily communications analyzing noteworthy events, including trends and recommendations
- Agentic Incident Response: Human-in-the-loop IR for common activities including resetting passwords, isolating hosts, and executing scans
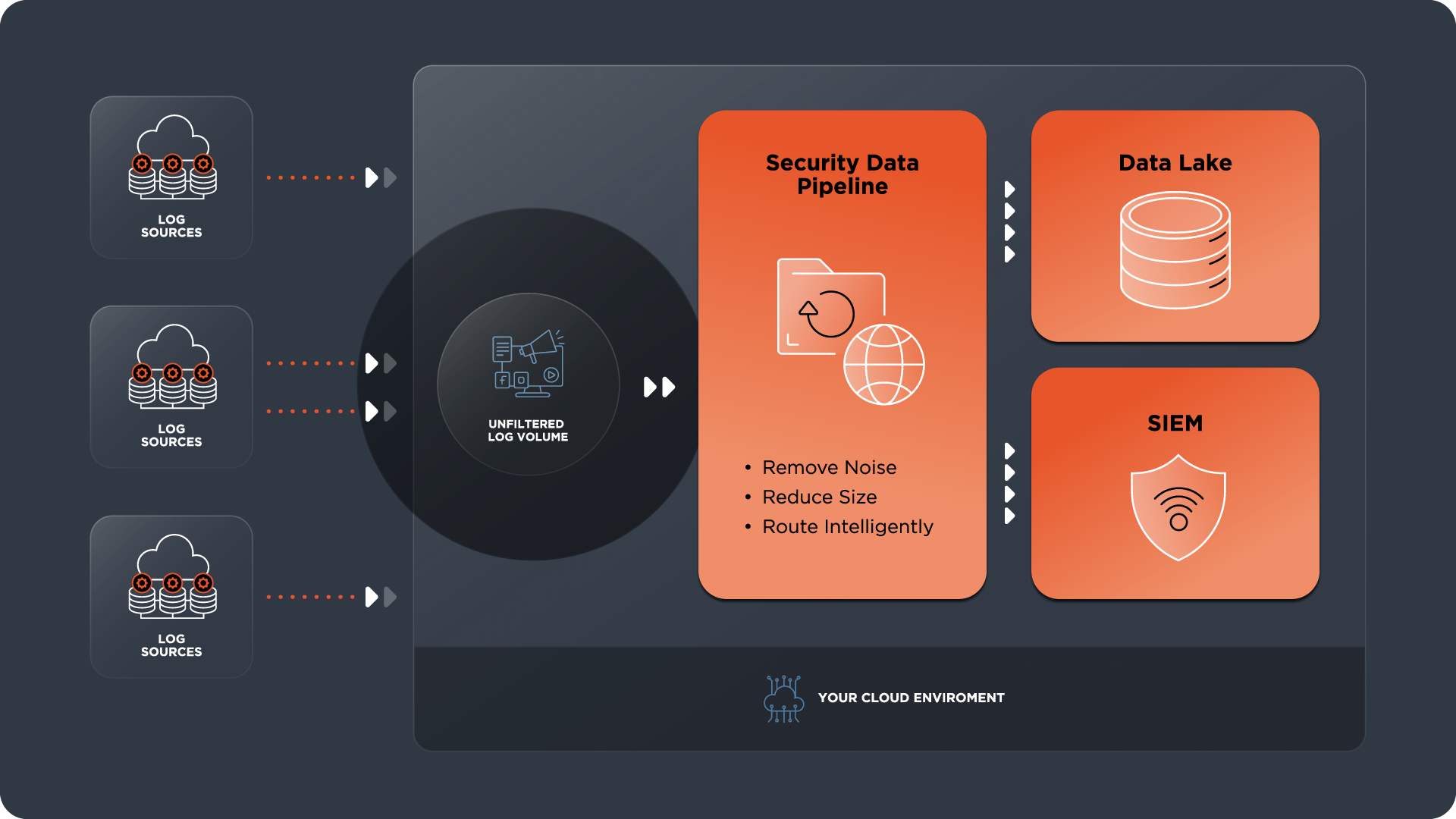
Modern Data Pipeline Management
- Log cleansing reduces noise by eliminating unnecessary fields within log files.
- Log routing only sends critical events to the SIEM, and the rest are sent to the Data Lake.
- Modern Data Pipeline Management cuts down log size and reduces ingest cost.
Monitoring and notification
SRA can perform 24x7x365 real-time monitoring for your environment. Our team of Defenders will correlate and investigate security events in our transparent workspace (you can see what we are doing).

Why SRA?
- People Forward Approach. We provide an experienced, world-class team. Your SRA team will not be assigned to many accounts and your alerts will not be managed by a pool of high-turnover analysts.
- We Build Lasting Capabilities. We work with your team collaboratively to recommend, inform, and assist with tuning efforts, as well as runbooks, response procedures, and use case documentation to improve detection and prevention capabilities. All SOC documentation and processes are yours.
- Follow the Sun. SRA is an international company and uses a “follow-the-Sun” model to provide consistent 24x7x365 coverage.
Related Blogs
Building Accessibility into VECTR
Discover how Security Risk Advisors integrated accessibility into VECTR, enhancing usability for keyboard navigation and screen readers while meeting WCAG AA standards. Learn about the challenges and solutions in building inclusive cybersecurity tools.
Intune Suite Is Included in E3/E5 Starting July 2026: What’s Included and How to Plan for Adoption.
Discover how the inclusion of Intune Suite in Microsoft 365 E3/E5 licenses starting July 2026 will transform endpoint management. Explore features like Advanced Analytics, Endpoint Privilege Management, and Cloud PKI, and learn how to plan for adoption effectively.
Examining the ExCYTIn-Bench Approach for Benchmarking AI Incident Response Capabilities
Explore ExCyTIn-Bench, a pioneering framework for benchmarking AI in cybersecurity investigations. Learn how advanced reasoning strategies and process engineering can enhance AI’s role in SOC workflows and incident response.







