The cyber threat landscape continues to evolve, and attackers aren’t slowing down. Organizations need to keep up and adapt to new threats through building detection content and engineering efforts.
But where do you start? What should be addressed first?
There are certain setbacks that can exist when working in the content development space, especially when engineers are being pulled in a million different directions. Whether it be too many items to tackle, no clear priority list, or the inability to track measurable progress with content creation, figuring out where to begin and how to approach a threat detection strategy can be difficult.
Purple Teams are a great starting point and help address most of these complications. Purple Team engagements help teams concentrate their efforts by simulating threats that are most relevant to the current threat landscape. Running these types of tests allows an organization to measure their threat resilience and assess their detection capabilities against common and emerging attack techniques. They also provide an initial benchmark, and with continued repeat testing, highlight progress as content gets pushed.
How Purple Teams Can Help Set Detection Engineering Priorities
The attackers aren’t slowing down, the security task list is growing faster than it’s getting checked off, so how do you get things back into a manageable state and make measured progress?
Identifying Visibility Gaps
One of the primary benefits of Purple Team exercises is identifying gaps in coverage and paths for improvement. Testing may reveal potential issues in logging and areas within a network where malicious activities might go undetected without regular Purple Teams. By simulating attacks, these engagements can pinpoint these blind spots, allowing organizations to prioritize the development of detection rules for these areas.
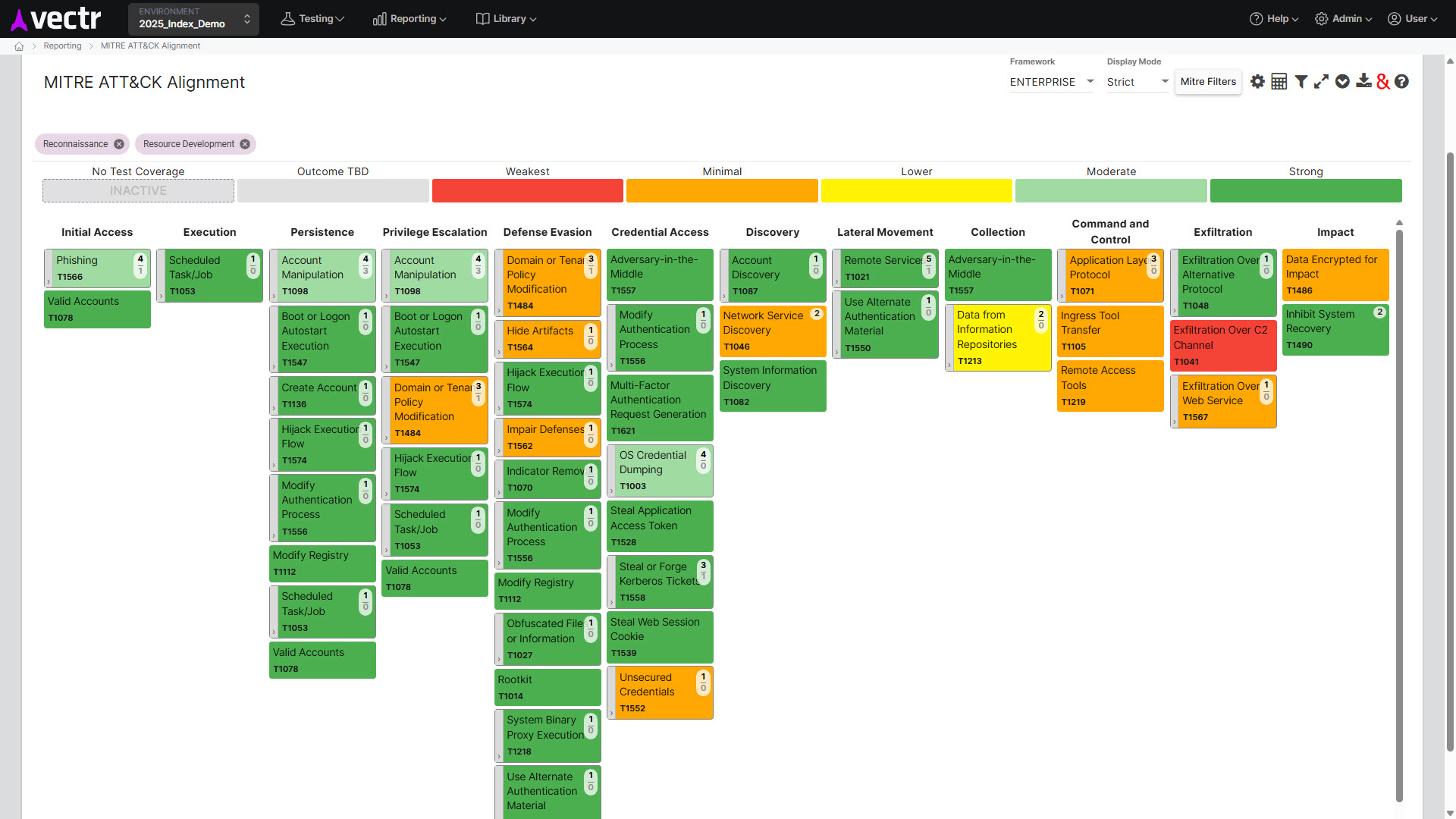
MITRE ATT&CK Heatmap in VECTR
Validating and Improving Existing Detection Rules
Purple Teams test existing detection and prevention rules by simulating various attack techniques. One goal of Purple Teams is to “inspect what we expect.” It is expected that existing controls will work as intended, but continuous testing helps to confirm this. These validation efforts ensure that detection rules already in place are effective in identifying malicious activities. If a detection rule fails to trigger during a test case, this indicates a need to adjust the rule or create new detection content. Items like this can be relatively low effort and easy place to start in terms prioritization. Often it is easier to adjust an existing rule than it is draft new content.

Test Case Panel in VECTR
Developing New Content
The insights gained from Purple Team exercises can be used to generate the necessary logs to develop new detection content. For instance, if a particular attack technique is not detected, detection engineers can create new rules to identify that type of activity in the future and be prepared for possible attacks. With VECTR™, organizations can track the defensive tools expected to block or detect certain test cases and determine if logging is present or not. Teams can prioritize remediation in instances where the logging exists, as it is easier to detect something that you have a log for than figuring out how to get those logs. This continuous development of detection content allows organizations to improve their security posture and stay up to date with the latest attack trends.
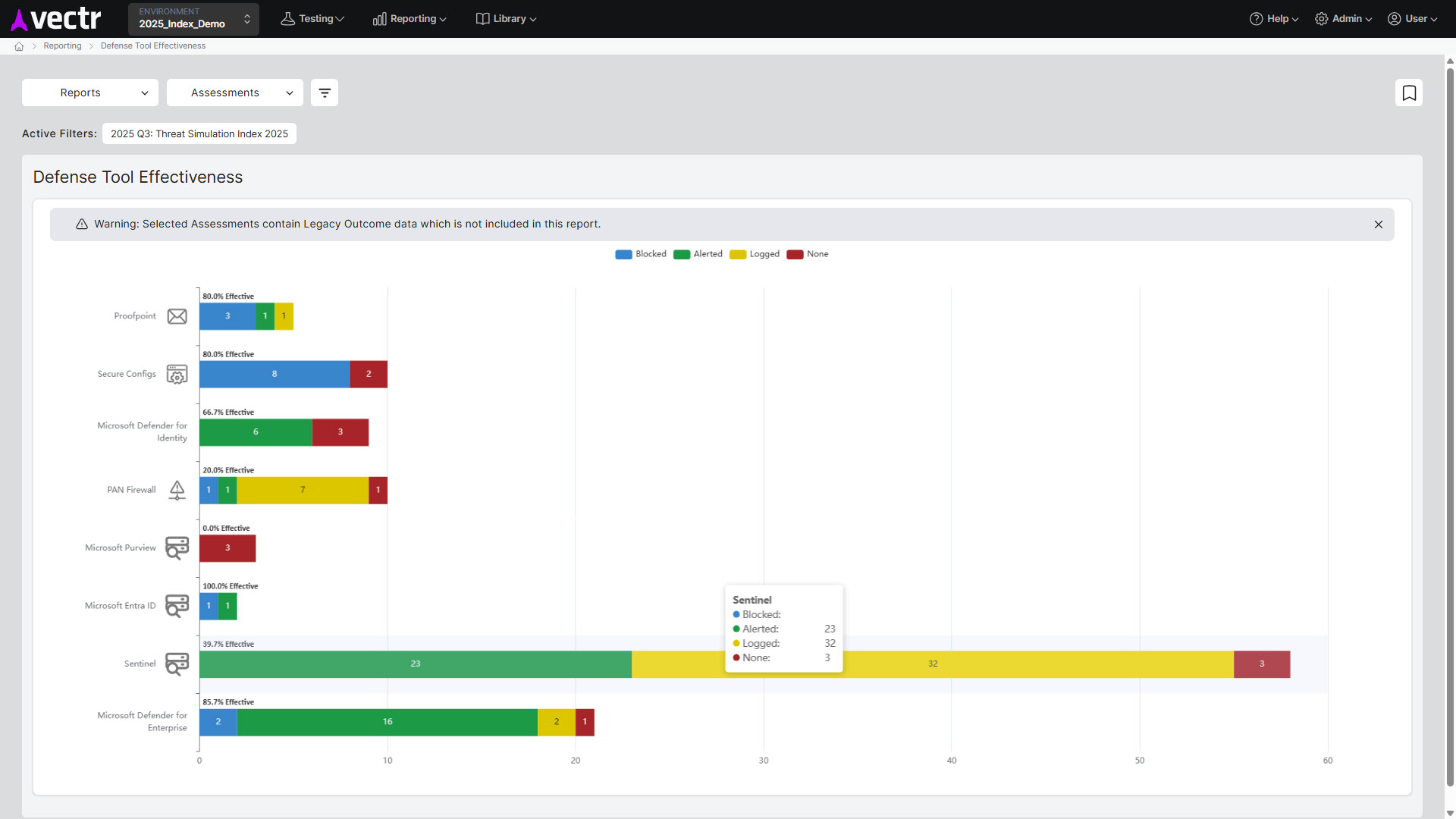
Defense Tool Effectiveness Report in VECTR
Prioritizing Solutions Based on Effort and Risk
Purple Teams help organizations determine which test cases to prioritize first, as some projects may be easier to complete than others. Some tests are also more critical than others based on the organization’s threat landscape and risk profile. Purple Teams help in prioritizing detection efforts by highlighting the most significant threats and areas of concern. For example, an organization may struggle with detecting/blocking certain Persistence or Defense Evasion techniques which fall closer to the initial stages of an attack chain versus Exfiltration or Command and Control techniques. Remediation efforts may shift to address missed test cases that are closer to initial access to stop an adversary early on in their attack. This prioritization ensures that the most critical security concerns are addressed first.
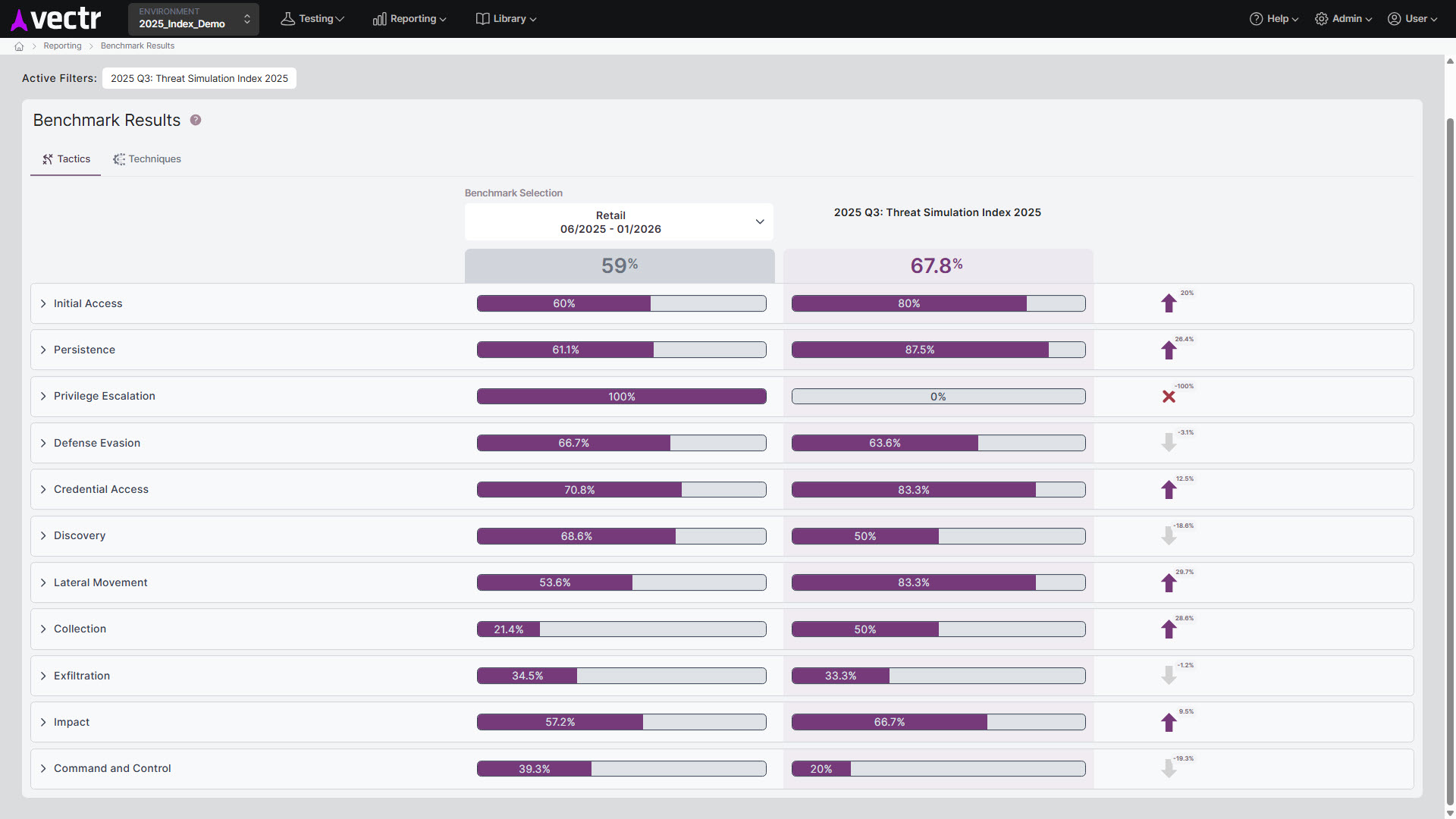
Benchmark Results Report in VECTR showing how your Purple Team outcomes compare to the Threat Index
Purple Teams Frequency and Cadence
Organizations can determine how often to run a Purple Team; however, SRA recommends running them 2-3 times a year. This cadence may depend on several different factors including team availability, strategic objectives, and what remediation efforts a team can accomplish in a short amount of time. Depending on an organization’s needs and environment, certain curriculum may be better suited to focus on than others. The VECTR™ test plans detail more information on the different indices available, which includes the 2025 Threat Index, as well as additional options such as Entra ID, AWS Cloud, Azure Cloud, and the Active Directory threat index.
Purple Teams play a crucial role in enhancing detection engineering efforts by combining the offensive expertise of red teams with the defensive strategies and knowledge of blue teams. By leveraging the insights gained from simulating real-world attacks, organizations can identify detection opportunities and prioritize their engineering efforts.
Alex Ioannidis
Alexandra focuses on EDR engineering and detection rule creation, specifically for SentinelOne, Microsoft Defender, and CrowdStrike. Alexandra is also a threat hunt lead, developing and overseeing threat hunts for multiple clients.
Alexandra is a graduate of Rochester Institute of Technology, holding a degree in Computing Security with a minor in Networking & Systems Administration.
Alexandra is also CySA+ certified.





