Hypothetical Scenario
You are an Identity and Access Management team member working at a hospital in New York undergoing an Merger and Acquisition. You’ve been asked to investigate the hospital’s current identity management controls and verify compliance status with New York Hospital Cybersecurity regulations Section 405.46. Do you know which users should have access to which resources? What are those users doing with that access? Are there organizational controls in place for managing access? Can auditors verify that the controls are working effectively?
While this scenario is specific to New York regulations, this problem is common throughout all industries. Most organizations have hundreds of solutions where access must be provisioned, reviewed, and deprovisioned. Centralizing multiple Identity Providers (IdP) has streamlined the provisioning and deprovisioning process but has not previously improved the process of reviewing users and groups’ permissions to individual applications.
As of right now, the above compliance requirements are specific to New York State. However, it would not come as a shock to many aligned security and privacy professions if this was to become an audited regulatory requirement within other states, frameworks, and compliance audits. Today, this requirement aims to enhance the security posture of the healthcare industry. However, in the future, it will significantly increase the analysis, communication, execution, and reporting tasks that organizations, often with limited security staff, will need to manage—a pre-existing concern in the healthcare sector. To help alleviate this concern there are solutions to help automate and streamline the access review workflow process such as Microsoft’s Identity Governance.
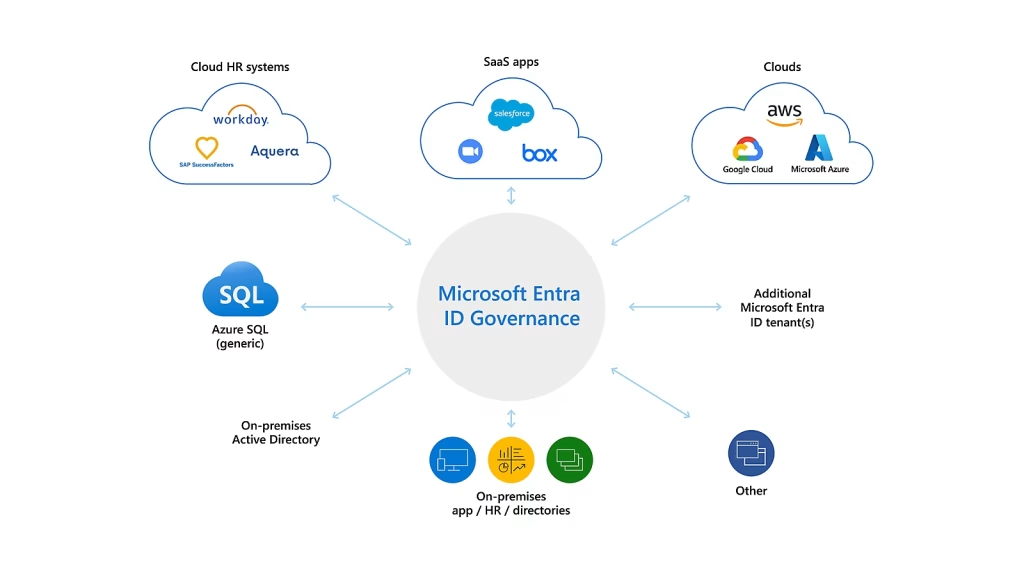
An image of compatible solutions and scenarios where Microsoft’s Identity Governance’s Access Reviews feature can be used.
Access Reviews is one of several P2 licensing solutions within the Identity Governance module (image 1), which analyzes previews, automates, and reports on steps which are typically performed manually by security personnel. Historically, enterprises have applied a decentralized approach to access reviews to maintain compliance with regulations such as Sarbanes-Oxley (SOX), Payment Card Industry (PCI), the Health Insurance Portability and Accountability Act (HIPAA) and many more. If proof of access reviews occurred among the at-risk population handling sensitive data types (for example, financial and healthcare), compliance could be achieved, however there was a high overhead cost as a result of constant user interaction, complex investigations, and laborious reporting processes. Consequently, this approach resulted in dilapidated enforcement processes, increased resource constraints, and generated inconsistent and unreliable data. All while maintaining low confidence in the users included in the review, the user’s response, and the approvers knowledge of the user’s access requirements.
Many organizations jumped onto the automation craze but did not understand their program requirements, directory hygiene, Role Based Access Control (RBAC) matrixes, and Identity Provider (IDP) connections. Once an organization has performed their review, identified their program requirements, and configured their directory structure (e.g., groups, users, and roles) to be as expected, an organization can consider using Microsoft’s Identity Governance Access Reviews to automate user access reviews.
What Features are Included in Access Reviews?
To utilize the Identity Governance Access Reviews module for performing reviews requires a P2 license or above and the Identity Governance Administrator role. Additionally, the items below are programmatic and configuration considerations when developing an Access Review within the Identity Governance portal including:
Program Considerations
- Who can create, manage, and approve the reviews?
- Who should be included in training for this workflow and how often?
- Once an Access Review has been configured how can it be used to inform identity management personnel and leadership during future decisions?
- How often should reminders be communicated to users and approvers within the workflow?
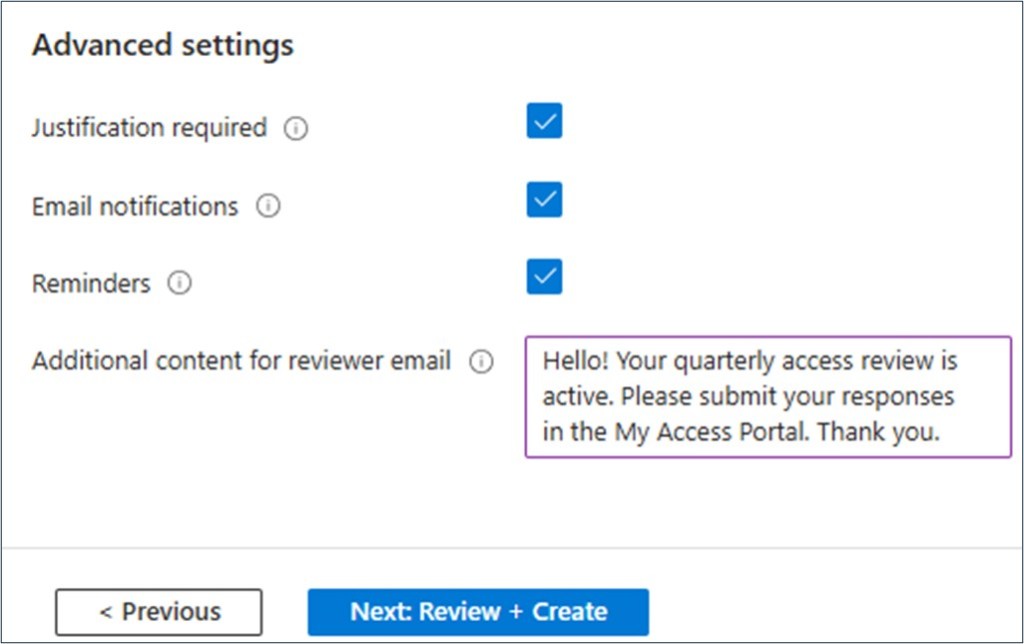
Customized notifications can be incorporated into the workflow to decrease the amount of time spent chasing users and approvers down to complete their individual tasks.
- What are the federal and/or state requirements for access review frequency?
Technical Considerations
- How often should the access review workflow occur?
- Who should have the ability to review access reviews? (e.g., manager, delegates, self-etc.)
- How much time does the identity, and reviewer allocate to submit and approve the review outcome?
- What happens when a response is or is not collected through the Access Review form?

Changes can be auto applied or provided within the CSV report upon the workflows completion. Additionally, the ‘Take Recommendations’ option can be used if the approver wants to incorporate quantitative data points from the users interactions. See the next bullet for more information.
- How does one know that the responders or approvers of the Access Review responded accurately? Should ‘Take Recommendations’ be applied to assist the approver with quantitative data points on the user’s access?
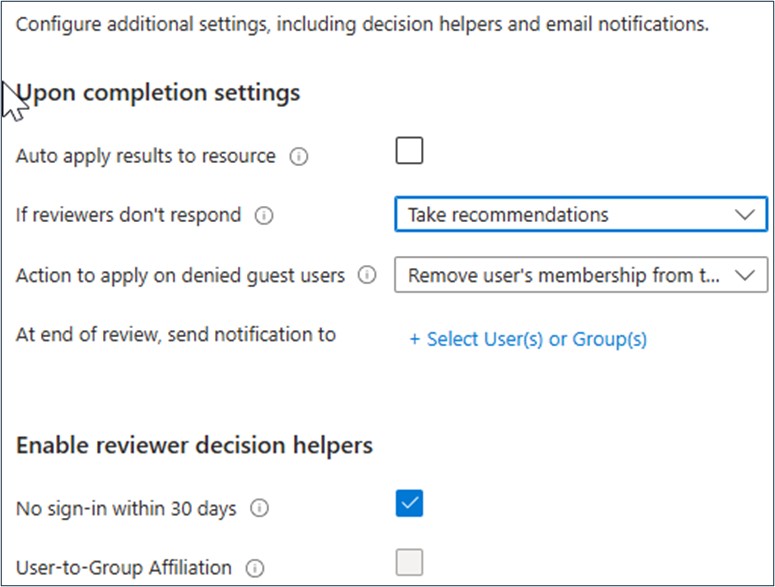
‘Take Recommendations’ can be selected to empower the approvers with additional ‘decision helpers’ when making their final decision about a user’s access requirements.
The items above are a few considerations to consider when developing and implementing Access Reviews. The complexity of this program can vary based on the industry, scope of users & applications, geographic compliance etc.
How can SRA help?
At SRA we’ve devised a custom solution using Access Reviews to assist organizations with designing, implementing, and reporting on organizational access review results. Our solution consists of three phases which include data collection, implementation, education & handoff. During data collection we dive into directory setup, existing Role Based Access Control (RBAC) matrixes, enterprise policies and standards, as well as collection of success factors to utilize during the implementation phase. The Implementation phase includes hands-on workflow creation and configuration, metric gathering, and reporting based on the success metrics defined in the initial phase. Finally, the handoff includes developing documentation on how to create, maintain, and disperse the workflows throughout an organization. Additionally, training materials are provided for administrators, approvers, and users interacting with the Identity Governance Access Review solution.
Conclusion
There are a vast number of applications in existence that require access, and there are only a limited number of individuals who can comprehend the complexities of implementing security controls for each, so you can see why organizations are heading towards automation to reduce overhead, improve visibility, and increase efficiency. Additionally, many organizations inherit and maintain a hybrid active directory structure as a result of mergers and acquisitions, which complicates implementation design and delays project completion. At SRA our custom solution leads organizations throughout the design, deployment, education, and reporting of enterprise applications based on the current state directory information. We also incorporate a training stage so that leaders, administrators, and team members can independently implement workflows in accordance with program requirements outlined in the initial design phase. This is designed to ensure that the workflow is adopted throughout the organization and the Return on Investment (ROI) is realized. If you or your team would like assistance in designing, implementing, and maintaining the Access Reviews workflows, contact us here.






