Policies and controls may help you sleep at night, but words and hope won’t stop a hacker. Hope that controls are properly implemented, and that policies are enforced only go so far, this is why Purple Teams have become a staple in mature security programs. Organizations need ways to quantify security posture, track regressions and improvements over time, and continuously validate effectiveness of tools and controls. Fortunately, Purple Teams, and the VECTR platform along with the Threat Resilience Metric, help make that possible, not only for on-premises environments, but Azure, AWS, and any other environment an organization would like to test.
Rarely would an organization not have any standard or control against external exposure, but what happens if an insider threat changes a control, or a misconfiguration causes an exposure unintentionally, or an APT manages to compromise credentials. This is where regular validation with Purple Teams can confirm if the Security team would have visibility and knowledge of such activity occurring. Below within VECTR, we can create a campaign, or grouping of test cases, in this case Public Storage Exposure. The intent of most Purple Team test cases is with appropriate access (assumed compromise), would the Security team detect and respond to such an event. Take the following three variations of Public Storage Exposure as an example.
- Creation of an Overly Permissive Token
- Attaching a Public IP to a Storage Account
- Set Storage Account Default Network Access to Allow

Real life examples of breaches serve as a good starting point for test cases such as an Overly Permissive Token. In late 2023, Wiz notified Microsoft of an overly permissive SAS token exposing Terabytes of data, Microsoft’s official response can be found here. Below is the VECTR test case page, where execution times, execution guidance, and outcomes can be recorded. For the blue team, options such as Blocked and Alerted are registered as successes, whereas None or Logged would be considered opportunities for improvement. These are example test cases and outcomes for the purpose of showing how reporting can enhance Cloud security.

An inside look into this test case shows the attack procedure was executed successfully but only logged by Sentinel not alerted or blocked. These results will be important when trying to quantify security posture and track results over time. As part of any individual assessment, VECTR can help show quantifiable results such as below. These results can be saved and reviewed over time. If the CISO or the board asks if the organization is protected from exposures like Microsoft’s, and a similar test case was performed in a previous Purple Team, one could refer back to the results as a reference. Below is an example of quantifiable metrics within VECTR.
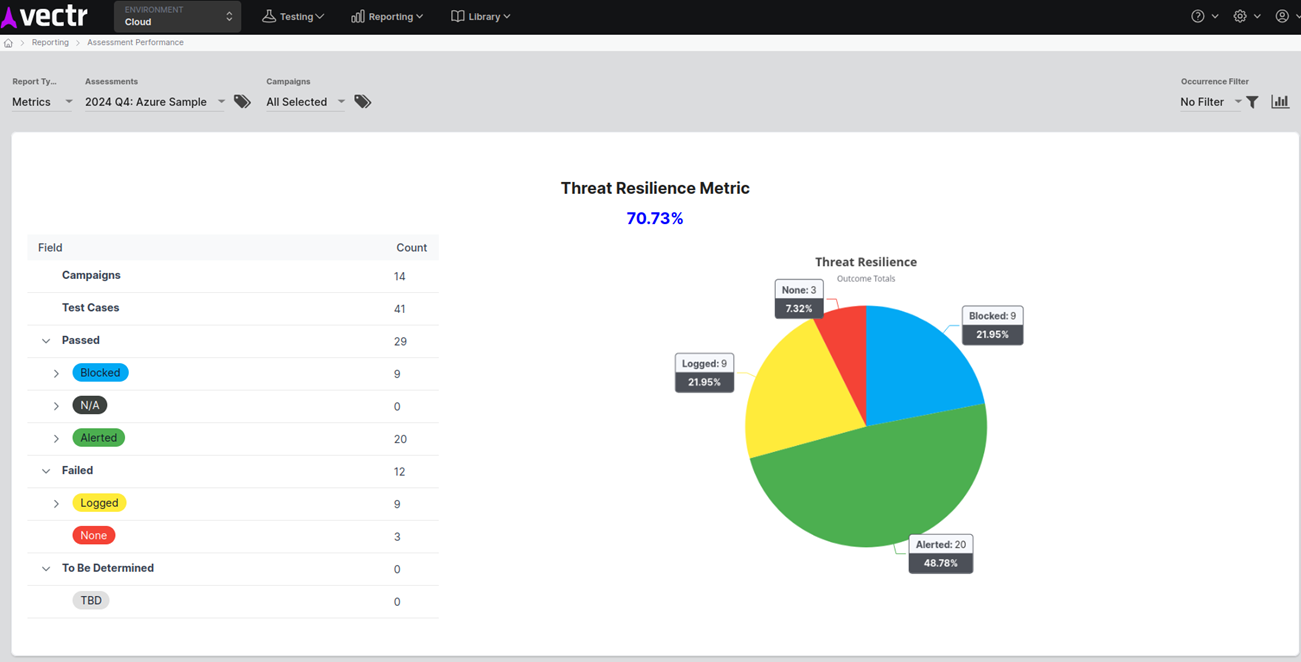
For organizations with multiple environments, these metrics can either be merged with filters or compared separately between each assessment, for example Azure vs AWS vs On-Premises.
These metrics are great for point-in-time reference, but environments are growing, shrinking, and changing as much as Security programs are, which is why consistent, regular Purple Teaming is highly recommended. SRA recommends at least a quarterly Purple Team to help validate historical controls and verify projected improvements. Below is a view of results over time, these views can be filtered several ways, below is a sample of this same campaign over a year’s time.

At SRA, we’re often able to help organizations increase their resilience metrics with tailored recommendations for specific control adjustments and/or tool configurations. However, we also often see regression in specific test cases due to an ever-changing environment like new applications or changes in controls. This is how Purple Teaming strategies like quantifying security posture, validating controls, and tracking results over time can enhance Cloud security and the Cloud security program. Don’t just rely on hope that tools and controls will keep your cloud environments secure. Test them, hold them to a high standard, and improve over time.
As a final note, ever wonder if you’re leading the pack or struggling to keep up? With VECTR Enterprise and SRA Purple Teaming) you can compare your results, benchmarked, with like sized organizations or even organizations within your industry such as Healthcare, Finance, Retail, OT, and others.
Brandon Martin
Brandon specializes in Incident Response, Advanced Threat Detection, Purple Teaming, and Strategic Initiatives. Having worked in varying Incident Response and Advisory roles for 10 years his expertise extends to a variety of leading enterprise tools in the following categories SIEM, EDR, AV, SOAR, CASB, CSPM, and UEBA.
Brandon holds several certifications such as ISACA Certified Information Security Manager (CISM), GIAC’s Incident Handler (GCIH), Detection Analyst (GCDA), and Network Forensic Analyst (GNFA). Using his experience and training Brandon helps organizations capitalize on the use of and collaboration between security platforms, configuration hardening, and organizational processes.
Brandon has experience with educational organizations, Fortune 500 corporations in healthcare providers, financial services, the energy sector as well as major insurance providers.





